Table of contents of the article:
Introduction
In March, we received reports from one of our customers laleggepertutti.it who complained of fraudulent clicks and related reductions in payments by advertising agencies.
We investigated with no little difficulty, leaving the task pending for about a week in order to enable a more detailed logging system and collect more data than the standard ones and better understand the problem complained of by the customer.
Providential was a second report from another of our client and webmaster Matteo Morreale di Jablabs.it that complaining of the same problem described above, thanks to his collaboration, has allowed us to cross data and make a differential analysis going to identify the problem in an extremely detailed way, arriving at identify the IP source authors of the fraudulent clicks on the ADS of the respective sites.
Analysis
From the analysis carried out, it emerged that an IP class is in the range 176.126.83.0 – 176.126.83.255 was the one accused and the author of the false clicks, most likely with the help of bot systems or equivalent automations.
The IP class in question as reported by the following whois:
% Information related to '176.126.83.0 - 176.126.83.255'% Abuse contact for '176.126.83.0 - 176.126.83.255' is 'info@oneprovider.com' inetnum: 176.126.83.0 - 176.126.83.255 netname: OneProvider descr: OneProvider country : IT org: ORG-OA765-RIPE admin-c: CP10803-RIPE mnt-domains: dagroup tech-c: CP10803-RIPE status: ASSIGNED PA mnt-by: dagroup mnt-by: ONEPROVIDER mnt-by: MNT-SEFLOW created : 2016-07-21T17: 32: 21Z last-modified: 2016-12-01T21: 19: 31Z source: RIPE organization: ORG-OA765-RIPE org-name: ONEPROVIDER org-type: OTHER address: 1500 Ste-Rose, H7S 1S4, Laval, Canada abuse-c: ACRO410-RIPE mnt-ref: WILLIAM-MNT mnt-ref: dagroup mnt-by: ONEPROVIDER created: 2016-03-07T23: 08: 42Z last-modified: 2017-02-03T15 : 51: 44Z source: RIPE # Filtered person: Charles-R Paquet address: 1500 Ste-Rose, H7K 1S4, Laval, Canada phone: +1.5142860253 10803 nic-hdl: CP2016-RIPE mnt-by: ONEPROVIDER created: 08-04-12T08: 28: 2016Z last-modified: 09-22-13T12: 59: 176.126.83.0Z source: RIPE% Information related to '24/49367AS176.126.83.0 'route: 24/49367 origin: AS2016 mnt-by: SEFLOW-MNT mnt-by: MNT-SEFLOW created: 08-04-22T45: 27: 2016Z last-modified: 08-04-22T45: 27: XNUMXZ source : RIPE
belongs to OneProvider, Canadian hosting provider present in various continents such as the European one that deals with the supply and rental of hosting services, Dedicated Servers and cloud.
Specifically if you look at the previous whois in more detail, it emerges as the class although assigned to OneProvider, is managed at the transit level (Transit ed) or connectivity provider, by an Italian provider in Cologno in the province of Lodi called SeFlow.
Of course we contacted the Italian connectivity provider SeFlow complaining of fraudulent activities from IPs that had references to their Hosting company, submitting a PEC and obtaining in response what we had already deduced from the previous whois.
Dear Marco,
thank you for contacting the SeFlow SOC department.The IP addresses indicated by you are not in use by SeFlow. As you can see by querying the RIPE database,
https://apps.db.ripe.net/db-web-ui/query?searchtext=176.126.83.250
the owner company is One Provider (at the link below you can find the references)https://apps.db.ripe.net/db-web-ui/lookup?source=ripe&key=ONEPROVIDER&type=mntner
SeFlow (among the many IP Transit companies they have) is just one of their connectivity providers.
We therefore invite you to communicate the abuse to One Provider, a usufructuary company and owner of the IP addresses indicated by you.We remain at your disposal for any clarification
Yours sincerely
Click fraud solution
Despite having reported the problem to OneProvider e not having any intention of waiting for an answer from them (among other things, never arrived) that could have opened hypothetical scenarios of legitimacy or otherwise of the request on a Canadian hosting provider, not Italian or even European (the fraudulent click activity is in fact of doubtful interpretation as there is no specific legislative reference that has global value) we decided to strive for ban the IP class '176.126.83.0 - 176.126.83.255' at the server level using the very common iptables (default firewall of GNU / Linux systems) free and present in all distributions of the well-known Open Source operating system.
The syntax is really very simple, and it was enough to issue the following command from the linux shell (and with root privileges), to see all the traffic of that range blocked:
iptables -A INPUT -s 176.126.83.0/24 -j DROP
The syntax is obviously specific for GNU / Linux systems but technically the same approach albeit with different commands and syntax can be applied using any hardware or software firewall and any operating system.
Solution for uncooperative hosting providers.
It is necessary to premise that although this command can be given without any problem on any vendor that grants you the ability to manage a Firewall, or any dedicated instance with administrative privileges (root in the case of GNU / Linux systems), it can present big but not insurmountable difficulties if the site victim of fraudulent clicks is hosted in a shared hosting (shared hosting) that unites in a single server many other customers as well as your site.
It is undisputed (although questionable) to say that blocking a range of IPs at the server level (therefore not only for your site but also all the others hosted on the same server) can be interpretable and subject to discussion, as what could be good for one customer it doesn't necessarily have to be for everyone else.
Many suppliers could in fact trash your legitimate request, with a more than legitimate motivation by appealing to net-neutrality rather than to a less professional and less motivated "laziness".
However, if you decide not to migrate the site to another hosting provider that can guarantee you the introduction of specific firewalling rules to block this type of fraudulent activity, you can always resort to specific solutions for the webserver that will allow you to block the offending range. eg using the .htaccess rules for Apache or LiteSpeed web servers.
To block the specific range, add the following to your site's root .htaccess file:
Deny from 176.126.83.0/255.255.255.0
If you use another webserver such as NGINX you will necessarily have to use your Hosting Provider or the features present (if enabled) in some control panels such as Plesk / cPanel / Directadmin (to name the most famous) and apply the block of the range .
For those who use CloudFlare or intend to do so, you can apply the rule directly from their control panel in the Firewall section and then Firewall Rules in this way:
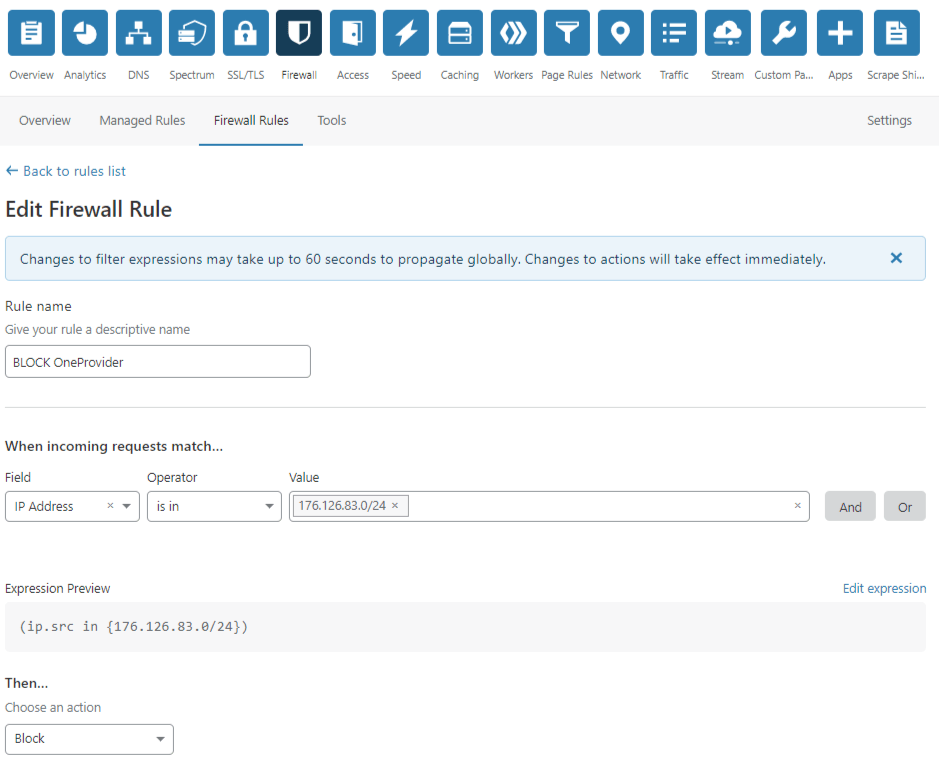
In short, the solutions can be very varied and essentially linked to the type of system you have and the related skills in implementing the blocking of IP authors of fraudulent clicks.
In case of doubts or hesitations, the assistance of qualified technical personnel will certainly put you in a position to operate safely in order to avoid problems deriving from a bad implementation of the filtering rules.
Some considerations on this.
Until now we have spoken in absolute and unobjectionable technical terms, however we feel entitled to hypothesize what may be the reasons for this fraudulent activity to the detriment of advertisers and publishers who find themselves important cuts on the monthly payouts of the dealerships.
What follows therefore are personal considerations, dictated by common sense and by reasoning as logical as possible aimed at identifying the motive for this fraudulent activity.
Given that having a server structure with a class C of dedicated IPs involves an economic investment, albeit not very high (we are in the order of a few hundred dollars) but in any case not free, one wonders what is the personal advantage of those who invest resources money and their time to set up bots that fraudulently click on the ADS of customer sites.
Considering that there is no way to obtain a direct economic advantage from this activity, it is common ground that the advantage obtained can instead be indirect.
One of the reasons, in fact, could be that of a strategy to generate discontent in the owners of websites that seeing significant sums cut in the monthly payout (even over 50%) in the item "Invalid traffic", could entice the site owner to pass to alternative advertising circuits.
In fact, it can be an alarm bell to receive a spontaneous proposal from some alternative advertising circuit following one or two months of fraudulent clicks.
It would certainly not absolutely prove a direct involvement in fraudulent click generation activities, but it would leave room for reasonable, albeit merely indicative, suspicions of what could have happened and how the apparent way out is actually part of the trap itself.
A real example on one of our clients
Here is for example what happened to Anna between 10 and 11 May 2021 (the complete identity was censored for privacy reasons) who saw her blog from over 1,5 million visitors per month (which deals with medical topics) being bombarded by clicks on the Google Ads ADS, arriving at not monetizing and seeing the Google advertising account suspended.

The content of the request was absolutely alarming as the customer was soon unable to continue the monetization of genuine traffic, spoiled by false clicks on Google banners (Click Fraud) and therefore seeing herself undermining a business that had hitherto been serene. and flourishing.
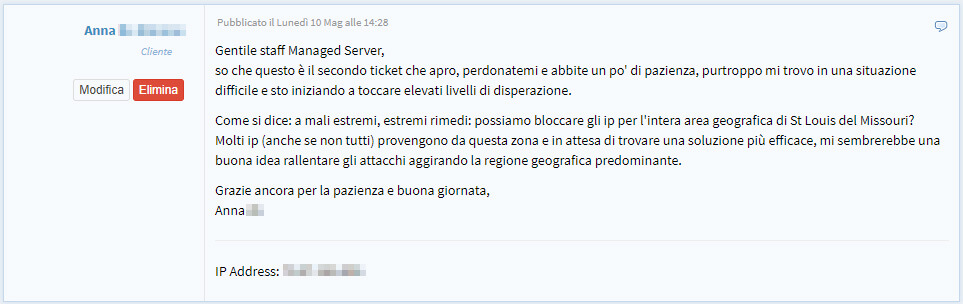
Obviously we understood the suggestion of the customer who, even if with non-technical skills in the field of networks and the Internet, certainly had guessed at least the logic in protecting herself.
We have therefore proposed an adequate solution by proposing an important value-added service that we offer to our customers.
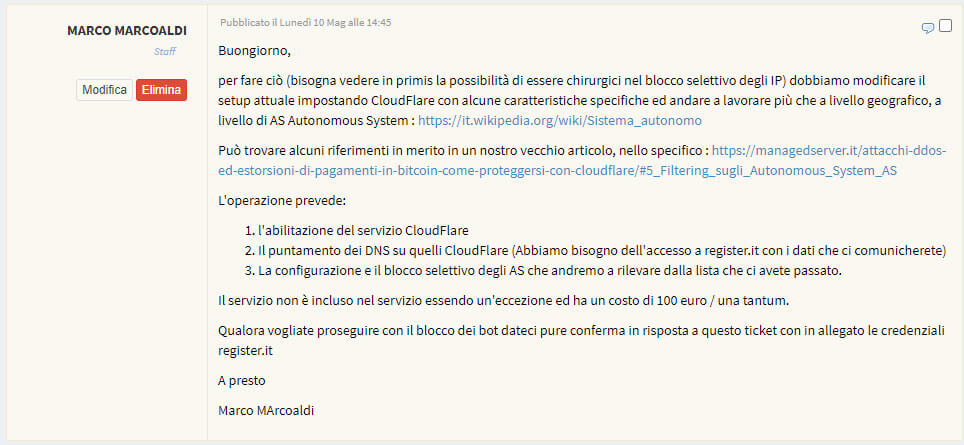
We worked by implementing several rules on the Web Application Firewall, creating a "selective combo" in order to filter real traffic from bot traffic in an extremely selective way due to false clicks.
After some reinterpretations and changes to the rules, we invited the customer to test after a few hours the effective quality of the filters put into production and the solution of the problem.
The customer answered us late in the evening sharing the joy of finally seeing this ugly attack ceased to the detriment of his serenity and his business.
It is obvious that beyond the mere economic return for our service, seeing satisfied and rejoicing a customer is something priceless.
Conclusions
Regardless of what may be the real reasons for the fraudulent click activities that are bombarding your site, reducing not only your monthly payout but also your personal peace of mind, our advice is to stop the problem by blocking the IPs that refer to the range indicated above.
In fact, blocking any fraudulent activity against you means not only applying the best solution for yourself but also for all the owners of sites who, to date, unaware of the phenomenon, continue to be silent victims of these activities, certainly to be condemned at least on an ethical and moral level. , hoping that with the collaboration and synergy of all the professionals and not, this problem will be definitively eradicated up to now.
