Table of contents of the article:
In the world of cybersecurity, especially in the web sector, one of the most insidious and persistent threats is represented by Cross-Site Scripting (XSS) attacks. These attacks exploit vulnerabilities in web applications to execute malicious code in the user's browser. To combat this threat, a powerful security tool has been developed: the Content Security Policy (CSP). In this article, we will explore in detail what CSP is, how it can be implemented, and its effectiveness in protecting websites from XSS attacks.
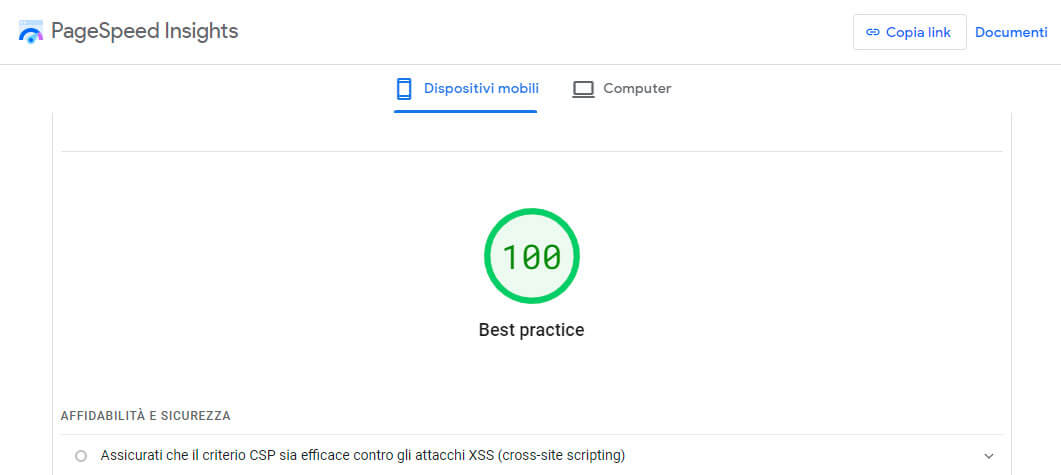
CSP has proven to be a crucial tool for improving web performance, an aspect of significant interest for those who manage CMS sites such as WordPress, Joomla or Drupal, as well as e-commerce platforms such as WooCommerce, Magento and Prestashop. Interestingly, the implementation of an effective CSP is also often suggested by Google PageSpeed Insights tests, highlighting the importance of this measure not only for security, but also for site performance.
Understanding Cross Site Scripting or XSS attacks
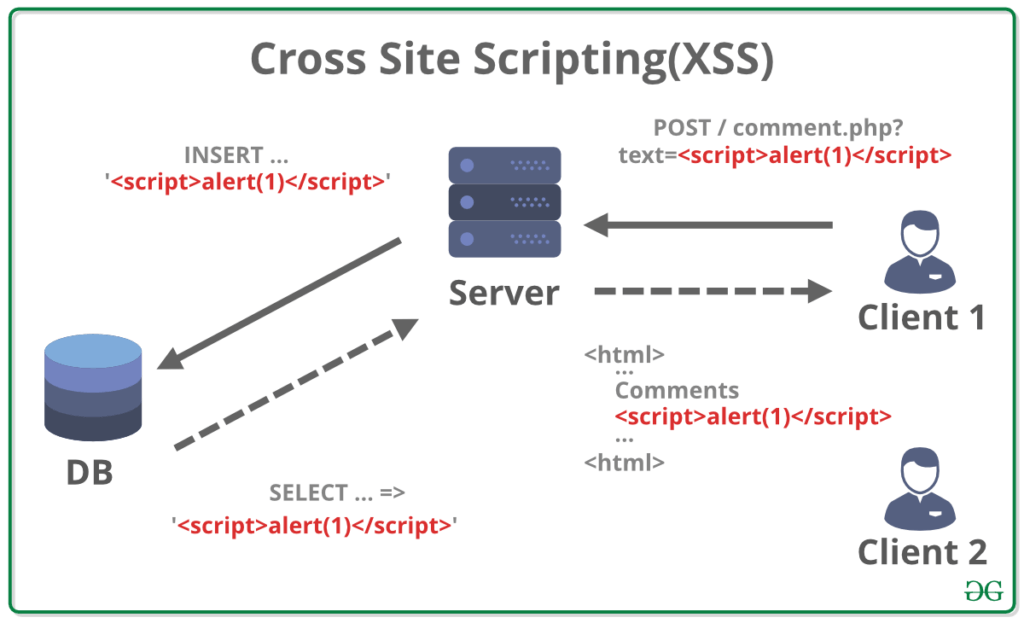
Cross Site Scripting attacks, also known as XSS, are one of the most common and dangerous threats in the web security landscape. These attacks occur when an attacker manages to insert or “inject” malicious scripts into web pages viewed by other users. The goal is to exploit the trust the user has in the website to execute malicious code in their browser.
Types of XSS Attacks
- XSS Reflections:
- They occur when an attacker tricks a victim into clicking on a link that contains malicious script. When the victim clicks on the link, the injected code is sent to the web server, which then reflects it back to the victim's browser, where it is executed.
- This type of attack is often used in combination with social engineering techniques to trick the user into clicking on a malicious link.
- Stored XSS (Persistent):
- In this scenario, the malicious code is saved on the web server, for example in a database or forum. When other users visit the specific site or page, the malicious code is loaded and executed in their browser.
- These attacks are particularly dangerous because they can affect multiple users and remain active for long periods.
- XSS Based on DOM:
- In these attacks, the malicious code is not processed by the web server, but is executed due to manipulation of the Document Object Model (DOM) in the user's browser.
- This type of XSS often occurs in dynamic web applications where the DOM is modified in response to user interactions.
How XSS Attacks Work
- XSS attacks exploit websites that accept user input and then return it without valid sanitization or escaping. This allows malicious scripts to be injected and executed in the context of the user's browser.
- Injected scripts can perform a variety of malicious actions, such as stealing session cookies, modifying web page content, or redirecting the user to malicious sites.
Security Implications of XSS Attacks
- XSS attacks can compromise the security of both users and websites. For users, they can result in the loss of sensitive data, such as login credentials or personal information.
- For websites, XSS attacks can damage reputations, undermine user trust, and potentially expose the organization to legal liability.
Prevention of XSS Attacks
- Preventing XSS attacks requires a multi-layered approach. This includes validating and sanitizing server-side inputs, client-side data escaping, and implementing security policies such as Content Security Policy (CSP).
- Training and awareness are also essential components in preventing XSS attacks. Educating developers about secure coding practices and users about online safety can significantly reduce the risk of attacks.
Understanding Content Security Policy (CSP)
1.1 Definition and Origins of CSP
Definition of CSP
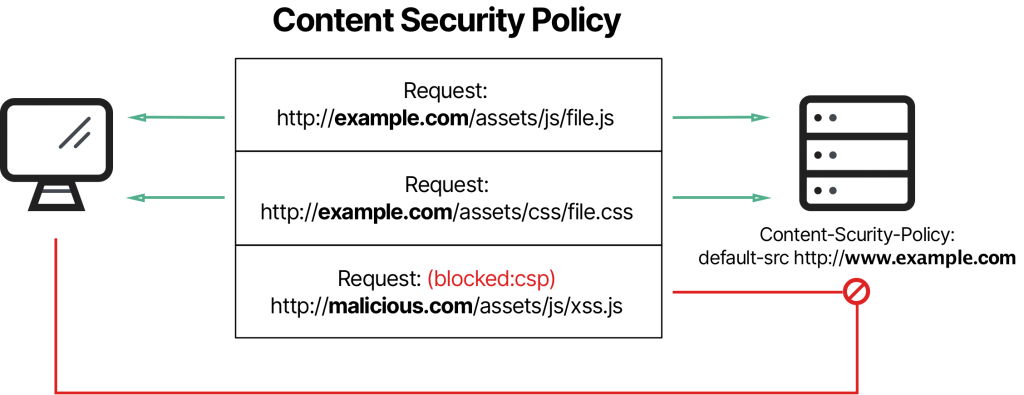
Content Security Policy (CSP) is a security measure designed to prevent a wide range of cyber attacks, especially Cross-Site Scripting (XSS) attacks. It works by allowing website managers to define a whitelist of trusted sources from which the browser can load content. This includes, but is not limited to, scripts, style sheets, images, and media.
Origins of CSP
CSP was first introduced as a standard in 2012. Its birth was due to the need to counter the increase in XSS attacks and to offer a more flexible and robust solution than existing security techniques. Initially, CSP had limited adoption due to its complexity and difficulty of implementation. However, as the years have passed and cyber threats have increased, it has become a standard tool for website security.
1.2 How CSP Works
Specifying Resources Using HTTP Headers
CSP operates through the use of HTTP headers. These headers, sent from the server to the browser, contain directives that specify the sources from which various types of resources are allowed to be loaded. For example, you can define safe sources for scripts, images, style sheets, and so on.
Browser Level Operation
When a browser loads a web page with a CSP active, it parses the HTTP headers it receives. It then follows the directives contained, blocking any resource that attempts to load from sources not listed in the CSP whitelists. This mechanism prevents the execution of malicious scripts or the loading of potentially dangerous content from unauthorized sources.
Flexibility and Configuration
A distinctive feature of CSP is its flexibility. Administrators can configure detailed CSP policies, specifying exactly which sources are considered safe for each type of content. This level of detail allows for customized security based on your website's specific needs.
1.3 Advantages of CSP in Web Security
Prevention of XSS Attacks
The most obvious benefit of CSP is its ability to prevent XSS attacks. By blocking the execution of unauthorized scripts, CSP prevents attackers from injecting malicious scripts into web pages, protecting both users and the site itself.
Protection from Other Vulnerabilities
In addition to XSS attacks, CSP offers protection against a variety of other vulnerabilities, such as clickjacking and malicious external resource injection. By providing granular control over the resources that can be uploaded, the CSP reduces the attack surface available to attackers.
Damage Mitigation from Unknown Vulnerabilities
Another significant benefit of CSP is its ability to mitigate damage caused by as yet unknown or unpatched vulnerabilities. Even if a vulnerability has not yet been identified or resolved, a well-configured CSP can prevent the exploitation of this vulnerability, thus providing a proactive defense against emerging threats.
Improved Compliance and User Trust
Implementing a CSP can also help an organization meet certain security standards and regulations, improving user trust and site reputation. In an age where data security is a growing concern, having a robust CSP is a clear sign that a site takes the protection of its users seriously.
Implementation of the Content Security Policy
2.1 Step by Step to Add a CSP
CSP implementation
Implementing a Content Security Policy (CSP) is crucial to strengthening the security of a website. The process involves adding the header Content-Security-Policy to the server's HTTP responses. This can be done in various ways, depending on your server environment and your site's specific needs.
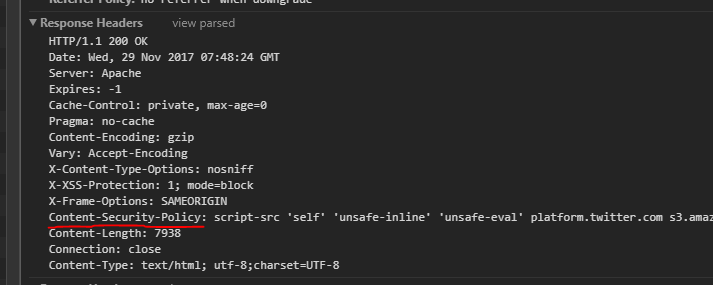
Addition of CSP Header
- Through the Web Server Configuration File: Most web servers, such as Apache or Nginx, allow you to add custom HTTP headers through their configuration files.
- For Apache: Edit the file
.htaccessor the site-specific configuration file (often located in/etc/apache2/sites-availableon Linux systems) by adding the following line: Header set Content-Security-Policy “default-src 'self'; script-src 'self' https://trustedscriptsource.com;”
This example specifies that all content must be loaded from the same document source (self), while scripts can only be loaded from the document source and fromhttps://trustedscriptsource.com. - For Nginx: Edit the server configuration file (usually located in
/etc/nginx/nginx.confor/etc/nginx/conf.d/) by adding the following line inside the blockserverolocation: add_header Content-Security-Policy “default-src 'self'; script-src 'self' https://trustedscriptsource.com;”;
- For Apache: Edit the file
- Via Server Side Scripting Languages: In environments where greater dynamic control is needed, you can opt to add the CSP header directly into the backend code. For example, in a PHP application, you can add the following code: header(“Content-Security-Policy: default-src 'self'; script-src 'self' https://trustedscriptsource.com;”);
Example of CSP Header
Suppose we want to create a CSP that allows loading scripts only from trusted sources and blocks everything else. The CSP header might look like this:
Content-Security-Policy: default-src 'none'; script-src 'self' https://trustedscriptsource.com; img-src 'self'; style-src 'self' https://trustedstylesource.com;
In this example:
default-src 'none'blocks all content by default, unless otherwise specified.script-src 'self' https://trustedscriptsource.comallows script execution only from the document source (self) and fromhttps://trustedscriptsource.com.img-src 'self'allows loading images only from the document source.style-src 'self' https://trustedstylesource.comallows loading of style sheets only from the document source and fromhttps://trustedstylesource.com.
Important Considerations
- Test Before Implementing: Before implementing the CSP in a production environment, it is crucial to test it in a development or staging environment to ensure that it does not block legitimate resources or break site functionality.
- Progressive Updates: Starting with a restrictive policy and gradually relaxing it can be safer than starting with a permissive policy.
- Monitoring and Maintenance: After implementation, monitor reports of CSP violations and update the policy accordingly to ensure it remains effective against new threats and site changes.
By following these steps, you can implement an effective CSP that significantly strengthens website security against various types of attacks, especially XSS attacks.
2.2 Test and Validate Your CSP
After implementing the Content Security Policy (CSP) on your website, it is essential to conduct thorough testing to ensure that the policy does not block legitimate resources necessary for the site to function properly. CSP testing is a crucial step because a policy that is too restrictive can break vital site functionality, while one that is too permissive will not offer the desired protection.
CSP Testing Process
- Using Browser Development Tools:

- Google Chrome Developer Tools: Chrome offers built-in tools that make it easy to identify CSP-related errors. After implementing the CSP, load your site into Chrome and open the developer tools (by pressing F12 or right-clicking and selecting “Inspect”).
- Sideboard: Once the developer tools are open, go to the “Console” tab. Here, Chrome will show any CSP violation errors. Each error will indicate which resource was blocked and which CSP directive caused the blocking.
- Network Tab: Also check the “Network” tab to see if some resources are not loading due to CSP. This can help you quickly identify loading issues related to CSP policies.
- Iterative Modification and Testing:
- Once you identify errors, modify your CSP policy to resolve them, allowing unexpectedly blocked legitimate resources to be loaded.
- Test the site again after each change to ensure that the problems have been resolved and that no new problems have been introduced.
- Use of Online Assessment Tools:
- There are various online tools that can help evaluate and test your CSP. These tools analyze CSP policies and provide feedback on their effectiveness and potential problems.
- Use these tools as part of your CSP review process to get a second opinion on your configuration.
- Monitoring of Violations in Production:
- After implementing the CSP in a production environment, consider using a reporting endpoint (
report-uri) in your CSP. This will allow users' browsers to send real-time reports in case of CSP violations. - Regularly analyze these reports to identify and resolve any issues that may not have been apparent during the testing phase.
- After implementing the CSP in a production environment, consider using a reporting endpoint (
- User Feedback:
- Sometimes, CSP problems are not immediately apparent. Listen to user feedback to identify any issues that may have been missed during testing.
Importance of Accurate Testing
Thorough testing of the CSP is crucial not only for security, but also for the usability of the site. A poorly configured CSP can lead to a frustrating user experience, with broken or missing site elements. Additionally, regular testing helps keep your CSP policy up-to-date with website developments and new security threats, ensuring your protection is always at the cutting edge.
2.3 Common Solutions to Problems in CSP Implementation
During implementation, it is common to encounter problems such as breaking some site functionality. In these cases, it may be necessary to refine CSP policies, adjusting or adding directives.
CSP and Protection from XSS Attacks
3.1 Analysis of XSS Attacks and CSP Response
Cross-Site Scripting (XSS) attacks represent one of the most widespread and dangerous threats in the web security landscape. These attacks exploit website vulnerabilities to execute malicious scripts in users' browsers, exploiting the user's trust in the visited site. XSS attacks can be mainly categorized into three types: reflected, memorized, and DOM-based. Each of these exploits different aspects of the interactions between the user, the browser and the website.
The Content Security Policy (CSP) represents one of the most effective responses against XSS attacks. It works by limiting the resources your browser can run or load to those you explicitly allow. For example, a CSP can specify that only scripts from the same source as the website can be executed, blocking any scripts inserted by third parties or loaded from external sources. This prevents attackers from executing malicious scripts in the user's browser, thus neutralizing the typical operating mode of XSS attacks.
3.2 CSP Strategies to Mitigate XSS Attacks
Implementing a CSP should be seen as part of a multi-layered defense approach to web security. While CSP is very effective at thwarting XSS attacks, its effectiveness increases when used in combination with other security techniques.
- Input Validation: Ensure that all user input is thoroughly validated and sanitized to remove or neutralize any malicious script injection attempts.
- Output Coding: When viewing user-supplied data, it is critical that it is encoded correctly so that any potentially malicious code appears as plain text rather than executing as script.
- Regular Updates and Patches: Keep website software, including CMS, plugins and themes, updated with the latest security patches to prevent exploitation of known vulnerabilities.
3.3 Examples of Effective CSP Implementations against XSS
Major websites, such as Google and Facebook, have implemented CSP as part of their defense strategy against XSS attacks. These implementations serve as benchmarks for other organizations and demonstrate the effectiveness of CSP in practice:
- Google: Google has implemented strict CSP policies in its web applications, such as Gmail and Google Drive, significantly limiting the possibility of unauthorized script execution.
- Facebook: Facebook has also adopted CSP, protecting its users from potential malicious scripts, especially in areas of the site where users can post content, such as posts.
These examples highlight how, through the adoption of CSP, it is possible to significantly increase the security of a website, even in the presence of high user traffic and complex interactions. For organizations looking to strengthen their web security, these success stories provide a clear demonstration of how implementing a CSP can be a critical element of an overall security strategy.
Conclusion.
In conclusion, addressing web security challenges, particularly Cross-Site Scripting (XSS) attacks, requires a thorough understanding and careful implementation of measures such as Content Security Policy (CSP). This tool not only serves as a barrier against cyber threats but also helps build a safe and reliable online environment for users.
However, properly configuring a CSP can be complex and require specialized knowledge, particularly for sites that use a wide range of dynamic content and scripts. A poorly configured CSP policy could not only fail to protect your site from attacks, but also negatively impact the functionality and performance of your site.
If you are facing difficulties in adding or optimizing a CSP policy for your website, our team of experts is here to help you. Specializing in Linux hosting and systems engineering, we are experts in optimizing web performance and managing security issues related to CMS sites such as WordPress, Joomla, Drupal and e-commerce platforms such as WooCommerce, Magento, and Prestashop.
Do not hesitate to contact us for advice or assistance in configuring your CSP. With our experience and expertise, we can help you navigate web security challenges, ensuring that your site is not only protected, but also performing and up to modern standards of web security and usability. Protecting your website from XSS attacks is crucial, and we are here to ensure you have all the resources you need to do so effectively.